I. INTRODUCTION
Radio Frequency Identification (RFID) system is a new wireless data transmission and reception technique for automatic identification, asset tracking, security surveillance etc. A typical RFID system is shown in Fig. 1.
A RFID system consists of three major components: a reader or integrator, which sends the interrogation signals to a RFID transponder or tag, which is to be identified; a RFID tag, which contains the identification code; and a middleware, which maintains the interface and the software protocol to encode and decode the identification data from the reader into a mainframe or a personal computer. Realising the fact that the barcode and other means for identifications and asset tracking are inadequate for recent demands, RFID technology has been taking the world of logistics, supply chain managements, asset tracking, security access control, and many other applications areas by storm. RFID was first proposed by H. Stockman [1]. He has introduced RFID systems in his landmark paper "Communication by Means of Reflected Power" [2]. Stockman advocates that considerable research and development works need to be done to solve the basic problems of wireless identification by means of reflected power [1].

Fig. 1 Block diagram of a typical RFID system.
RFID is a multi-disciplinary technology which encompasses a variety of disciplines. These include RF and microwave engineering, RF and digital integrated circuits, a big chunk of load bestows on the antenna technology followed by software and computer engineering for encoding and decoding of analog signals into meaningful codes for identifications and real time tracking. Due the flexibility and numerous advantages of RFID systems compared to barcodes and other identification systems, so far, RFID is now becoming a major player in mass market. Patronization for RFID technology by major retail chains like Wall Mart, K-Mart, USA Department of Defence, and similar consortia in Europe and Asia has accelerated the progress of RFID technology significantly in the new millennium. As a result, significant advancement on RFID technology has been gained within a short period of time. The RFID market has surpassed a few billion dollars mark recently and this growth is exponential with its diversified applications in all sectors like medicine and health care, agriculture, livestock, logistics, and retail chains etc... Today, RFID is being researched and investigated by both industry and academic scientists and engineers around the world.
The Massachusetts Institute of Technology (MIT) founded the AUTO-ID centre to standardize RFID thus enabling faster introduction of RFID into the mainstream [3]-[5] of retail chains, identification and asset management. Automatic Identification (Auto-ID) of items and livestock is required by many areas of government, commerce, science, industry and farming. As for an example, Australia has its comprehensive National Livestock Information System (NLIS) [6]. Under the umbrella of NLIS, every animal and pet in Australia must be e-tagged. Recent outbreak of mad cow disease and ban of imported beef from some countries, have forced Australia to adopt NLIS. These recent enforcement by private and government sectors has pushed RFID technology in the fore-front of development and implementation in almost all sectors of businesses and service industries. Therefore, it can be concluded that the applications of RFID involve the tracking of livestock, personal identification, area security, road tolling, supply chain management and logistics. Large corporations such as Wall Mart have taken significant steps to automate their supply chain management and logistics using Auto-ID [7]-[8]. As a result, thousands of manufacturers, suppliers and logistic support organizations of Wall-Mart are adopting the RFID technology for their goods, products and services. For any new technology, return of investment (IOR) is very crucial for any organization. Being a wireless system, RFID has been going through harsh scrutiny for reliability and security. With the advent of new anti-collision and security protocols, efficient antenna and RF/microwave systems, these problems are being delineated and solved.
Limitation of Barcodes and Emergence of RFID as an Enabling Technology Barcode labels have been used to track items and stocks for sometime after their inception in the early 70’s. Though barcodes are printed in marks and spaces and very cheap to implement, they impose undeniable obstacles in terms of their short range readability and un-automated tracking. These limitations are costing large corporations millions of dollars per annum [9]. The growing tendency today is to replace the barcodes with RFID transponders which have unique ID codes in order to identify items. Hence, the obstacles of reading range and automation would be solved using RFID. The only reason why RFID tags haven’t replaced the barcode is due to the price of the tag which is still much higher when compared to the price of the barcode. Hence, a huge amount of investments and investigations focusing on lowering the price of the transponder have been put in motion, and the price of the RFID tag is getting lower and lower every year. The development of chipless transponders without silicon integrated circuits (ICs) has lowered the cost of the tags even more, but at the expense of requiring smarter and agile RFID readers. Today’s RFID readers are comprised of (i) smart antenna systems, (ii) dedicated digital signal processing units, (iii) embedded systems alongside with (iv) middleware and (v) networking features. These features allow easy integration of RFID readers in data networks complying with standardized data transfer protocols. With versatile applications, range and speed of data communications, the operational frequency and coding techniques used by RFID readers are very widely spread - from low frequency (LF) systems to microwave systems. This creates a problem in having a ubiquitous RFID system and acceptance of global standards. In Generation 2 tags a unified approach has been formulated to remove the bottleneck and make the tag universal like the barcodes. To this end RFID readers play significant role in reading tags with various formats and standards.
In this paper we present a comprehensive review of RFID readers found on today’s market with a novel classification of RFID readers. This classification is based on the RFID readers’ reading capabilities, mobility, power supply, communication interface, data encoding protocols etc. The paper is organized as follows: section II presents the RFID reader system architecture_the fundamental building block of the RFID reader. The detailed descriptions of various RFID readers available on the market are presented in Section III.
The growing tendency towards creating a universal reader is presented in Section IV followed by conclusions in Section V.
II. RFID Reader System Architecture
Figure 2 shows the data flow of the RFID system architecture. RFID readers are devices that perform the interrogation of RFID transponders. In a passive RFID system the RFID reader supplies the tag with essential power in order for it to perform modulation of the reader’s interrogation signal. Therefore, the reader and transponders are in a master-slave relationship where the reader acts as a master and the transponders as slaves. Nevertheless RFID readers themselves are in a slave position as well. A software application, also called middleware, processes data from the RFID reader, acts as the master unit and sends commands to the reader. This means that all activities of the reader and transponder are initiated by the application software. In a hierarchical system structure the application software such as enterprise software [10] represents the master while the reader, as the slave, which is only activated when it receives a command from the application software, and therefore, the reader perform read or write operations of RFID transponders that are in its interrogation area.

Fig. 2 Master-slave principle between the application software and reader, and the reader and transponders
RFID systems can be classified as passive and active tag systems [11]. Powered by batteries active tags have on-board signal amplification and modulation facilities. Passive tags are batteryless and rely on the reader’s radiated energy to do some minor tasks of modulation and transmission of data. Therefore, active tags do not rely on the reader as much as passive tags do. As a result, active tags enjoy much superior performances in interrogation and data transmission due to their independence of power supply on a reader. In a passive tag system, a reader needs to have a powerful radiation field so that the passive RFID transponder can effectively cull sufficient power to perform some minor signal processing functions.
An RFID reader consists three main parts shown in Fig. 3. These main three components are:
• Control section;
• High frequency (HF) interface; and
• Antenna.
At the user end, the reader is connected to the host application such as enterprise software.

Fig. 3 Block diagram of a typical RFID reader.
Figure 4 shows the block diagram of the reader control section. The control section of the RFID reader performs digital signal processing and procedures over the received data from the RFID transponder. Also, the control section enables the reader to communicate with the transponders wirelessly by performing modulation, anticollision procedures and decoding the received data from the transponders. This data is usually used to interrogate tags (read) or to reprogram the tag (write). This section usually consists of a microprocessor, a memory block, a few analog-todigital converters and a communication block for the software application.
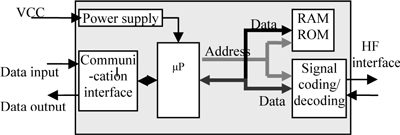
Fig. 4 Block diagram of the RFID reader control unit
Figure 5 shows the HF interface module of a RFID reader. The high frequency interface of the reader is used for RF signal transmission and reception. HF interfaces are consisted of two separate signal paths to correspond with the two directional data flows from and to the transponder.
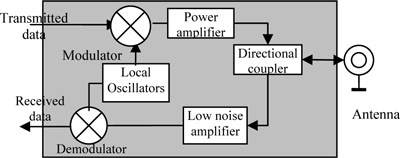
Fig. 5 Block diagram of the HF interface of a RFID reader operating in the 2.4 GHz ISM band.
The local oscillator generates the RF carrier signal, a modulator modulates the signal, the modulated signal is amplified by the power amplifier, and the amplified signal is transmitted through the antenna. A directional coupler separates the system’s transmitted signal and the received weak back-scattered signal from the tag. A directional coupler consists of two continuously coupled homogenous wires, and if all ports are matched, the power of the incoming and outgoing signal is divided in the coupler [12]. The received backscattered signal is weak and the low noise amplifiers increase the signal’s amplitude before and after the signal is decoded in the demodulator. The HF interface is one of the most complex sections of the reader. Most HF interfaces are protected from EM interference using metal cages. Different demodulation techniques are used when decoding the data received from the transponder. Most RFID systems operate using binary phase shift keying (BPSK) [13] and amplitude shift keying (ASK) [14]. A simple HF interface for a continuous wave (CW) RFID reader operating in the 2.45 GHz Industrial, Scientific and medical (ISM) band, using ASK demodulation is shown in Fig. 6. The reader transmits a CW signal at 2.4 GHz ISM band. Therefore, the transmit section needs not to be connected with the control section as shown in Fig. 5 The CW signal is amplified with a PA and the amplified continuous wave signal is transmitted via the antenna to the tag.

Fig. 6 Block diagram of a RFID reader operating at 2.45 GHz with ASK demodulation technique.
The radiation intensity of the reader antenna determines the interrogation range and zone. Depending on the RFID system’s applications the RFID reader can be designed in different ways where the antenna’s resonating frequency, gain, directivity and radiation pattern can vary. Antennas are spatial filters. Adaptive antennas are a promising technique for implementing this spatial diversity into RFID readers. Article [15] reports an adaptive antenna for RFID reader. This antenna is a 5-element rectangular patch antenna array with an intelligent beam forming network at 2.45 GHz. A number of different reader antennas have been developed during the years based on microstrip patch antennas [17]-[18], [20].
Following is a detailed discussion on various RFID reader systems available in the open literatures.
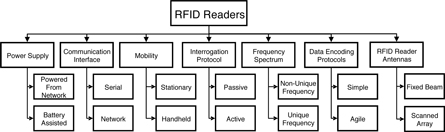
Fig.7 Classification of RFID readers available on the market.
III. Classification of RFID Readers
Fig. 7 shows the classifications of RFID readers available in open literature and commercial markets. The classification is done after an analysis and synthesis of a comprehensive literature review on RFID readers.
The classification is based on the power supply, communication interface, mobility, tag interrogation, frequency response, and the supporting protocols of the reader.
(a) Power Supply
The classification of the RFID reader based on their power supply brings forth two types of readers:
• readers supplied from the power network;
and
• battery powered (BP) readers.
Readers supplied by the power network generally use a power cord connected to an appropriate external electrical outlet. Because RFID readers are electronic devices, they need DC voltage supply for their electronic circuits and components. This means that an appropriate AC/DC adapter is used for the power supply of such readers. Most readers that use this type of power supply are fixed stationary readers and their operating power supply ranges from 5V-12V [21], but there are examples of readers that operate at voltage levels as high as 24 V [22].

Fig. 8 BP Alien Technology reader ALR-2850. Courtesy of Alien Technology Corporation, 2006. www.alientechnology.com.
Battery powered (BP) readers are light in weight and portable. The battery is mainly used to power up the motherboard of the reader. Most BP readers are handheld, but there are stationary readers that are battery assisted as well. BP readers use from 5V up to 12V batteries for their power supply [16]-[17]. Fig. 8 shows a BP reader from Alien Technology.
(b) Communication Interface
RFID readers can be classified on the basis of the interface that a reader provides for communication. Based on this communication interface, readers can be classified as:
• Serial; and
• Network.
Serial readers use a serial communication link to communicate with their host computers or software applications. The reader is physically connected to a host computer using the RS-232 [25], RS-485, IC2 or USB serial connection [26][28]. Serial readers have the advantage of being more reliable for data transmission than network readers. The disadvantage of serial readers is that they are limited by the number of serial ports at the host side. It might be needed to have a large number of host computers to connect all of the serial readers. In addition, the serial RS-232/485 cable is limited in size. Another problem is data transfer rate which is lower than network data transmission rate.
Network readers are connected to the host computer via a wired or wireless network (Fig. 9). These types of readers behave like a standard network device and do not require particular knowledge of the hardware and system configuration. Today’s RFID readers support multiple network protocols such as Ethernet, TCP/IP, UDP/IP, HTTP, LAN, WLAN and others [29]-[30]. This allows easier tracking and maintenance of the readers installed in the system. For example, if the readers implemented in the network need updating or the firmware and drivers are being reinstalled with a new driver version, this is easy to perform just by selecting the device from the host computer using the network connections window. This also provides a smaller number of hosts for installing a large number of readers in comparison with serial readers. The number of readers or their placement in the system environment is not determined or restricted by the wired connection as it is the case with RS-232/485 connections. The data transmission rate of network readers is far greater than that with serial readers (up to 10Mbps for Ethernet) and thus data is collected at a higher rate. The disadvantage of network readers is that the communication link is not as reliable as serial communication. When the communication link goes down, the back end cannot be accessed. As a result, the RFID system might come to a complete standstill. RFID readers have internal memory to store received data from the tags, so short time network failures may be compensated.

Fig. 9 UHF stationary Mercury4 network reader from ThingMagic. Courtesy of ThingMagic. www.thingmagic.com
(c) Mobility
The next classification of RFID readers can be made on their mobility. Hence, we distinguish two types of readers:
• Stationary; and
• Handheld.
Stationary RFID readers are also known as fixed readers. This term comes from the reader’s ability to be mounted on walls, portals, doors or other objects where they can perform effective transponder readings and are not meant to be moved or carried. Fixed RFID readers are mainly used for wireless data capture in supply chain management, asset tracking and product control [31]. Today’s fixed RFID readers are used for personnel identification and authentication for restricted access areas installed and mounted on portals and doors [32]-[33] as well. Most stationary readers support multiple protocols for transponder reader communication and can operate in standalone and in networking mode. A new trend involving the design of stationary readers places multiple antenna connections for connecting more than one antenna to the reader, allowing the user to achieve greater and diverse radiation patterns of the reader’s interrogation zone. They use power supply from 12V DC up to 24V, weigh from 1.5 kg up to 5kg and can achieve reading ranges up to 300 m [34].
Handheld RFID readers are mobile readers that can be carried and operated by users as handheld units. Handheld readers have built in antennas and usually do not have connectors for additional antennas. They are battery powered and are light weight (from 82g up to 700g). They have shorter reading ranges than fixed readers (up to a 100 m) [35]. Handheld readers are used in tracking live stock (farm animals such as pigs, sheep, goats and cows), locating items in stores and in stock, etc [36]. They communicate with the host computer using wireless communication protocols and contain memory blocks to save data. After the user finishes data capturing, it enables data transfer from the reader to a database via wired communication. Most handheld readers have the ability to call out to a specific transponder and even they can locate a transponder in regard to the location of the handheld RFID reader. Handheld RFID readers are also integrated with barcode scanners so that users can perform both tag and barcode identification simultaneously. A handheld reader by SAVI Technology [36] is shown in Fig.10.

Fig. 10 A handheld reader by SAVI Technology
(d) Interrogation Protocol
Another classification of RFID readers can be made upon the reader’s interrogation protocols in terms of being:
• Passive; and
• Active.
Passive readers are limited to only "listening" and do not perform additional tag interrogations. A passive reader’s block diagram is shown in Figure 6. These readers are often called "dumb" readers. When interrogating the tags, the reader sends CW signal as a power source for data processing for the RFID transponder. The transponder provides data transmission, which is a unique ID code, hence no message or command is needed from the RFID reader. Protocols or data transmission techniques between the tag and reader that are characterized in this manner are called transponder driven protocols due to the passive role of the reader in the interrogation process. Transponder driven protocols for communication with the reader are implemented in tags in the form of ALOHA based protocols [37].
ALOHA is a simple multi-access procedure, which got its name from the fact that the procedure was developed for the ALOHANET in the 1970’s. The basic operating principle of this protocol is that as soon as a data packet is available it is sent from the transponder to the reader. The ALOHA protocol is categorized as a transponder-driven stochastic Time Domain Multiple Access (TDMA) procedure. The procedure is used with read-only transponders, which generally have to transfer only a small amount of data (ID), this data being sent to the reader in a periodic sequence. The data transmission time occupies only a fraction of the repetition time.
This timing varies slightly for individual transponders. There is, therefore, a certain probability that two transponders can transmit their data packets at different time slots and the data packets will not collide with one another. One possibility of optimizing the relatively slow throughput of the ALOHA procedure is the Slotted ALOHA procedure. In this procedure transponders may only begin to transmit data packets defined in synchronous points in time (slots). This is therefore an interrogator driven stochastic TDMA procedure.
The period in which a collision can occur in the Slotted ALOHA procedure is smaller than it is in the case of the simple ALOHA.
Active readers are true interrogators which interrogate and listen to tags depending on the number of tags and communication protocols embedded in the system for data transmission between the tags and the readers. Active readers are more capable and "agile" than passive readers. These active readers are complex in design in regards to both software and hardware implementations. Other than just providing a power source and medium for the transponders to operate and transmit data, active readers perform data transmission towards the tags which is implemented, in most cases, as a modulation of the carrier signal. Therefore, transponders must have a demodulating circuitry enabling them to decode the reader’s command. Active readers are commercially available and are mainly found in the form of handheld readers for product identification. These readers can perform both listening and calling out to the tags and can even achieve successful area location of the transponder based on the amplitudes of the transponders respond to the reader’s interrogation. Most active readers that combine transponder listening and calling use binary search algorithms. The implementation of a binary search algorithm requires that the precise bit position of data collision is recognized in the reader. In addition, a suitable bit coding is required (NRZ, Manchester coding, etc). The block diagram of an active RFID reader is shown in Figure 11.

Fig. 11 Components of an active RFID reader.
The transceiver is responsible for sending the reader’s signal to the surrounding environment and receiving the response back from the tags. The transmitter sends RF power (effective isotropic radiated power_EIRP) and the reader’s command via its antenna to the tag which is situated in the reading zone. The receiver receives the analog signals from the tag via the reader’s antenna. It then sends the signals to the reader microprocessor, where it is converted to an equivalent digital signal. The microprocessor thus decodes the received analog signal and performs data processing. It also encodes and modulates the reader’s carrier signal when it wants to send out a message to one particular tag or toward all of the tags in the interrogation zone. In addition, the microprocessor could contain custom logic for doing low-level filtering and additional data processing [38]. The memory block is used for storing data such as the reader’s configuration parameters and a list of tag reads. Hence, if the connection between the reader and host computer goes down, not all read tag data will be lost. The communication interface provides the communication instructions for the reader and allows it to interact with external entities and modules. A reader could have a serial as well as a network interface communicating with the external modules such as the host computer. These types of readers have been analyzed in detail in the previous section.
(e) Frequency Spectrum
Besides using their carrier frequencies to perform data transmission and reception, RFID reader’s also use other frequency bands. Most readers send out commands to tags on a certain frequency band and receive the transponder’s response on a different frequency band (usually a 2nd harmonic or a frequency division of the original reader’s interrogation frequency). Therefore we can classify readers based on the transponder frequency responses that they listen to as:
• Unique frequency response based readers;
and
• Non-unique frequency response based
readers.
Unique frequency response based readers operate at a defined frequency range and use this frequency for both data transmission and reception. The vast majority of RFID readers that can be found on the market today are unique frequency response based readers.
None-unique frequency response based readers operate using one frequency for sending a command or just provide a carrier signal at a certain frequency and listen for an integer multiple of its carrier frequency, generally in the form of a 2nd harmonic, or a frequency divided signal as the transponder’s response [39]. Two RF frequencies used for communication by the reader to the RFID system allows fast and reliable full-duplex communication, but this system needs a more complex RF front end for both the reader and transponder module. Some RFID systems are designed in such a way that multiple frequency use is enabled by using multiple antennas operating at different but predefined frequencies [40]. Figure 12 shows a multi-frequency RFID system.

Fig. 12 Block diagram of a RFID system operating at multiple frequencies.
(f) Data Encoding Protocols
RFID readers can use multiple frequencies for data transmission and reception but they can also use multiple protocols to communicate with transponders. Therefore we can classify RFID readers based on their ability to communicate with transponders using diverse protocols.
We can distinguish between two types of RFID readers based upon their ability to communicate with transponders in regards to data encoding protocols:
• Simple RFID readers; and
• Agile RFID readers.
Simple RFID readers use a unique protocol for communication and data transmission between transponders in the reader’s interrogation zone [41]. When a transponder that supports the reader’s interrogation protocol is set in the interrogation area of the reader, the tag is automatically recognized and detected. When a transponder that operates using a different protocol is put into the interrogation area, no data transmission will occur, because of the unfamiliarity of the reader’s interrogation protocol to the transponder. The advantage of simple RFID readers is that they are easy to debug due to the fact that their interrogation protocol is unique and they have greater tag reading speeds (up to 2000 tags per second) [42], but they lack flexibility and cannot interact with different types of RFID systems due to their ability to support only one protocol.
Agile RFID readers can operate and perform interrogations and data transmission with transponders using multiple protocols. Agile readers enable users to use a reader from one manufacturer and transponders from other manufacturers, which is sometimes a necessity. Some agile reader manufacturers allow programming the reader using special reader system software that enables the user to increase the number of protocols used by the reader for tag interrogation and therefore create a more powerful and efficient reader. The most commonly used protocols for data transmission between transponders and readers are EPC Gen1 [43], EPC Gen2 [44], ISO 18000 [45], TIRIS Bus Protocol, etc. The advantage of agile readers is their ability to read tags from different manufacturers, enable diverse RFID system implementation, they input flexibility into the RFID system, but they require a more complex data and signal processing architecture and advanced software support. A majority of RFID readers that can be found in the market are designed for multiple protocols and multi-tag readings [46].
(g) RFID Reader Antenna
The efficiency of the RFID reader in terms of transponder interrogation and detection is highly dependant on the reader antenna. We can distinguish between two types of RFID reader based on their antennas:
• Fixed beam RFID reader; and
• Scanned array RFID reader.
Fixed Beam antennas are characterized with a unique and fixed beam radiation pattern [16]. Most RFID readers are equipped with omni-directional or wide beamwidth antennas in order to cover as much area as possible. The use of several fixed beam antennas is used as well, and can be commonly found in Alien Technology readers. The advantage of using such antennas is that they are easy to install and do not need any logic to control their radiation patterns. The disadvantage of these antennas is that they pick up multipath signals alongside with the transponders signal which can result in errors during interrogation.
Scanned Array RFID readers use smart antenna systems in order to reduce the number of transponders within their main lobe radiation zone thus reduce reading errors and collisions among tags. This technique exploits spatial diversity among tags’ locations. The direct beam also reduces the effects of multipathing [19]. This is due to the fact that phased array antennas can have a controlled radiation pattern and are highly directional, so it is possible to introduce spatial diversity into transponders’ interrogations. The effects of multi-pathing can be reduced by the use of directional antennas. This new approach to RFID antenna technology is being incorporated by a few RFID manufacturers such as Omron Corporation, Japan [52], RFID Inc. [53] and RFSAW, USA [41]. In March 2006 Omron Corporation developed a new electronic control antenna technology in there UHF band RFID reader systems [52]. RFID tags are subject to multipath interference_an inherent problem of electromagnetic signals. Multi-path interferences make an RFID tag unreadable even if it is within the reading range of the reader. To solve this problem, a new type of antenna technology is used that can electronically control the main beam emitted from the reader’s antenna. This smart antenna technology incorporated in RFID readers has reduced reflections from surroundings and thus minimized the degradation of the system performance due to multipath and other undesired effects. RFID Inc. [53] has introduced a 32element compact package smart antenna with associated switches at 125 KHz. This new product advances RFID applications in factory automation, process controls and original equipment manufacturer (OEM) markets.
So far we have presented various types modern RFID readers available in the market. Next we are going to present the next generation of RFID readers which are based on universal RFID reader chip sets.
IV. Toward the Universal Reader Design
Barcodes have been enjoying a robust global standard and have free movements across boundaries. FRID being an enabling and maturing technology lacks this flexibility. Manufacturers in different countries have been following their own standards and procedures, but Gen 2 RFID tag systems have set standards so tags can be read across boundaries. An interesting trend has been observed in RFID reader manufacturers in developing universal RFID readers and modules [47]-[48]. These readers are generally designed as independent circuit boards with defined output pins, communication interface and can be equipped by different antennas depending on the users needs. The main aim of this type of reader is to enable maximum design flexibility and diversity to the user and to allow easy-to-implement reader modules to speed up the design and setup of modules of an RFID system. Most reader modules operate on 5-9 V dc power supply, use RS232/422/485 communication interface, some have WLAN and Bluetooth protocols embedded in them, some allow full duplex (FDX) or half duplex (HDX) communication, have a short read range (up to a few meters) and weigh from 5g up to 100g. Their applications are aimed mainly toward the design of handheld readers, but can be effectively used when designing stationary readers as well. A Texas Instrument’s micro RFID reader module is shown in Fig. 13.

Fig. 13 Micro RFID reader module by Texas Instruments. Courtesy of Texas Instruments Incorporated 2006.www.ti.com
RFID reader designers and manufacturers have gone a step further in the design of independent reader modules. The design of embedded RFID readers has been introduced to the world of RFID in 2005 [49]. The basic idea of embedded RFID readers is to increase transponder reading flexibility and create a "universal reader". In June 2005, Anadigm Inc. announced the birth of the industry’s first RFID embedded reader that can be customized to read different RFID tag types, with different modulation schemes, frequencies and data transmission protocols [50]. The "universal" reader is an in-house developed product of Anadigm Inc., and is named RangeMaster. The RangeMaster’s system-level block diagram is shown in Fig. 14. It comprises a Field Programmable Analog Array (FPAA) in conjunction with an RFID State Machine, enabling RFID system engineers to develop a universal RFID reader supporting multiple protocols and frequencies for future fixed, mobile and handheld reader designs [51]. The advantage of embedded RFID readers, such as RangeMaster, when compared to standard readers is that they allow standardization around a single circuit board, simplification and improvement of product development, manufacturing time and cost.

Fig. 14 RangeMaster’s system-level block diagram.
V. CONCLUSION
RFID is an enabling technology transforming the identification, asset tracking, security surveillance, medicine and many other sectors. This paper has presented a comprehensive literature review of RFID readers. This comprehensive review has generated a few new findings:
• Analysis and synthesis of various RFID readers developed recently by various commercial companies. This classification is based on the unique features of RFID readers. They are power supply, communication interface, interrogation protocol, frequency response of tags and data encoding protocol. To the best of the authors’ knowledge such comprehensive classification based on the available literature in various resources were not presented before.
• This new synthesized classification will help the end users to plan and select RFID reader according to their applications and requirements hence will develop confidence in investment of return in using the RFID enabling technology in their manufacturing plants, supply chains, logistics, asset tracking, security and medical diagnostics.
• The current bottleneck of using RFID technology is its lack of global standard like barcodes. Gen2 tag system will overcome this limitation. Already some manufacturers have paid attention to this issue and started designing such universal systems that can be used across the boundary of countries and applications.
REFERENCES
[1] J. Landt, Shrouds of Time. The History of RFID, AIM Inc. publications, October 2001 http://www.aimglobal.org/technologies/rfid/resource s/shrouds_of_time.pdf (accessed March 2006)
[2] H. Stockman, "Communication by Means of Reflected Power", Proceedings of the IRE, pp: 11961204, October 1948.
[3] D. McFarlane, Y. Sheffi, The Impact of Automatic Identification on Supply Chain Operations, International Journal of Logistics Management, vol. 14, no. 1, 2003.
[4] M. Karkkainen, T. Ala-Risku, Automatic Identification – Applications and Technologies, Logistics Research Network 8th Annual Conference, London UK, September 2003.
[5] K. Finkenzeller, RFID Handbook 2nd Edition, John Wiley & Sons, Ltd., 2003.
[6] National Livestock Identification System, official website, www.nlis.mla.com.au
[7] Sun Microsystems, Inc., Sun and Auto-ID, Sun Microsystems white paper <'
[8] EPCglobal, Inc., The EPCglobal Network: Overview of Design, Benefits and Security, EPCglobal white paper http://www.epcglobalinc.org/ (accessed April 2006)
[9] D’Hont S., The Cutting Edge of RFID Technology and Applications for Manufacturing and Distribution", Texas Instruments white paper, http://www.ti.com/rfid/docs/manuals/whtPapers/man uf_dist.pdf (accessed March 2006)
[10] Mark Palmer, "Build an Effective RFID Architecture" http://www.rfidjournal.com/article/articleview/781/1 /82/ (accessed 24 June 2007)
[11] S. Preradovic, N. C. Karmakar, "RFID Transponders – a Review" Proc. ICECE ’06 International Conference on Electrical and Computer Engineering, pp: 96-99, Dhaka, Bangladesh, December 22-26, 2006
[12] D. M. Pozar, Microwave Engineering – 3rd Edition, John Wiley & Sons, Inc., 2005.
[13] F. Kocer, M. P. Flynn, A Long-Range RFID IC with On-Chip ADC in 0.25 /spl mu/m CMOS, Digest of Papers 2005 IEEE Radio Frequency Integrated Circuits (RFIC) Symposium, pp:361-364, 12-14 June, Long Beach, California, USA, 2005.
[14] N. C. Karmakar, S. M. Roy, S. Preradovic, T. D. Vo, S. Jenvey, Development of Low-Cost Active RFID Tag at 2.4GHz, 36th European Microwave Conference, pp:1602-1605, 10-15 September, 2006.
[15] P. Salonen, L. Sydanheimo, A 2.45 GHz Digital Beam-forming Antenna for RFID Reader, IEEE 55th Vehicular Technology Conference, vol. 4, pp. 17661770, Birmingham, Alabama, USA, May 2002.
[16] P. Salonen, M. Keskilammi, L. Sydanheimo, M. Kivikoski, An Intelligent 2.45 GHz Beam-scanning Array for Modern RFID Reader, IEEE International Conference on Phased Array Systems and Technology, pp. 407-410, Dana Point, USA, May 2000.
[17] S. K. Padhi, N. C. Karmakar, C. L. Law, S. Aditya, A Dual Polarized Aperture Coupled Microstrip Patch Antenna with High Isolation for RFID Applications, 2001. IEEE Antennas and Propagation Society International Symposium, vol. 2, pp. 2-5, Boston, USA, July 2001.
[18] G. Marocco, Gain-optimized Self-resonant Meander Line Antennas for RFID Applications, Antennas and Wireless Propagation Letters, vol. 2, pp. 302-305, 2003.
[19] S. K. Padhi, N. C. Karmakar, C. L. Law, Dual Polarized Reader Antenna Array for RFID Application, 2003. IEEE Antennas and Propagation Society International Symposium, vol. 4, pp. 265-268, Columbus, Ohio, USA, June 2003.
[20] R. Hornung, ARLON FoamClad Based Microstrip Patch Antennas and Arrays for RFID Readers, ARLON internet white paper, http://www.arlonmed.com/Foamclad%20for%20RFID.pdf#search='mi crostrip%20antennaRFID%20reader' (accessed May 2006)
[21] CHIPSILICON Pty. Ltd, Product information internet site, 2006.http://info.chipsilicon.com:8080/chipsilicon/ products/ (accessed May 2006)
[22] Omron Canada Inc., Microwave RFID system V690 data sheet, 2005. http://www.omron.com (accessed March 2006)
[23] Alien Technology Corporation, BAP ALR-2850 reader data sheet, 2005. http://www.alientechnology.com/products/rfid_reade rs.php (accessed February 2006)
[24] AVANTE International Inc., AVANTE Handheld RFID Reader product info, 2006. http://www.avantetech.com (accessed March 2006)
[25] Dallas Semiconductor MAXIM, Application note 83: Fundamentals of RS-232 Serial Communications, March 2001. www.maxim-dallas.com (accessed March 2006).
[26] Feig Electronic Gmbh, Product information internet site, 2006. http://www.feig.de (accessed March 2006)
[27] Idesco, IR8000 reader data sheet, May 2005. http://www.idesco.fi (accessed March 2006)
[28] Smart Code Corporation, Product information internet site, 2006. http://www.smartcodecorp.com/products/ rfid_readers.asp (accessed April 2006)
[29] Samsys Technologies Inc., UHF reader MP9320 v2.8e data sheet, 2005. http://ww.samsys.com (accessed March 2006)
[30] Thingmagic Corporation, Product information internet site, 2006. http://www.thingmagic.com/html/prod.htm (accessed February 2006)
[31] Symbol Corporation, XR480 RFID reader data sheet, 2006. http://www.symbol.com/XR480 (accessed March 2006)
[32] TAGSYS Corporation, Product information internet site, 2006. www.tagsys.com/html/rfid-53.html (accessed March 2006)
[33] Tagmaster, LR-3 reader product data sheet, 2006. http://www.tagmaster.com (accessed March 2006)
[34] RF Code, Inc, Mantis II Active RFID reader data sheet, 2006. http://www.rfcode.com/433mantis_reader.asp (accessed April 2006)
[35] IDENTEC SOLUTIONS, Inc., i-CARD CF Mobile reader data sheet, 2006. http://www.savi.com/products/ds.smr650.pdf (accessed March 2006)
[37] V. Naware, G. Mergen, L. Tong, Stability and Delay of Finite-User Slotted ALOHA with Multipacket Reception, IEEE Transactions of Information Theory, vol. 51, issue 7, pp: 2636-2656, July 2005.
[38] C. Nak-Gwon, L. Hyuek-Jae, L. Sang-Hoon, K. Seong-Jeen, Design of a 13.56MHz RFID System, ICACT 2006 The 8th International Conference of Advanced Communication Technology, vol. 1, Phoenix Park, Korea, February 2006.
[39] ActiveWave Inc., Product information data internet site, 2006. http://www.activewaveinc.com/products_rfid_reader s.html (accessed March 2006)
[40] R. Page, A Low Power RF ID Transponder, Grand Prize Winner 1993 RF Design Awards Contest, Wenzel Associates, 1993.
[41] BALOGH RFID, HYPER X LMB-6012 RFID reader data sheet, January 2003. http://www.balogh.cc/HyperX/Support/PDF/LMB60 12-6013.pdf (accessed March 2006)
[42] RFSAW, Inc., RFSAW RFID system data sheet, 2003.www.rfsaw.com (accessed April 2006)
[43] Impinj, The Gen 2 Story: Charting the Path to RFID that Just Works, White Paper, 2005 Impinj, Inc. http://www.impinj.com/files/MR_GP_ED_00001_G en2Story.pdf (accessed June 2007)
[44] EPC Global, EPC Radio-Frequency Identity Protocols Class-1, Generation-2 UHF RFID Protocol for Communications at 860 MHz-960 MHz – version 1.0.9, Internet Article, EPCglobal Inc, January 2005. http://www.epcglobalinc.org/standards/Class_1_Gen eration_2_UHF_Air_Interface_Protocol_Standard_Ve rsion_1.0.9.pdf (accessed June 2007)
[45] Alien Technology, EPCglobal Class 1 Gen 2 RFID Specification, Internet Whitepaper, Alien Technology Corporation, 2005. http://www.alientechnology.com/docs/AT_wp_EPC Global_WEB.pdf (accessed June 2007)
[46] EE Times Asia, RFID Solution Enables Single Universal RFID Reader, Internet Article, January 2006. http://www.eetasia.com/ART_8800403199__NP_79 8750a5.HTM (accessed June 2007)
[47] Texas Instruments, Inc., Series 2000 Micro Reader data sheet, 2002. http://www.ti.com/rfid/docs/manuals/pdfSpecs/RISTU-MRD1.pdf(accessed June 2006)
[48] Sentinel ID Systems, Inc., Product information internet site, 2006. http://www.sentinelid.com/products.html (accessed March 2006)
[49] M. Reynolds, C. Weigand, Design considerations for embedded software-defined RFID readers, internet white paper, August 2005. http://www.thingmagic.com/html/508EWTF2.pdf#s earch='508EWTF2 (accessed April 2006)
[50] Electronic Engineering Times, Anadigm Rolls Universal RFID Reader, internet site, June 2005. http://www.eetasia.com/ART_8800368056_499491_a 7168a56.HTM (accessed March 2006)
[51] Anadigm Inc., RangeMaster Solution for RFID Tag Readers, Anadigm product data sheet, 2005. http://www.anadigm.com/_doc/GF0411000001.pdf#search='anadigmrangemaster'(accessed March 2006)
[52] T. Nakamura, J. Seddon, Omron Develops World’s First Antenna Technology That Bossts UHF RFID Tag Read Performance, Omron Corporation press releases, http://www.omron.com/news/n_270306.htmlC (accessed June 2007)
[53] Profibus-DeviceNet-Ethernet IP-Modbus-Remote I/O, http://www.rfidinc.com (accessed June 2007)
