The modern battlefield depends on secure wireless for voice, data and increasingly, in the era of autonomous vehicles and drones, streaming video. Soldiers need to quickly access video footage even in low bandwidth environments without it being tracked, intercepted or manipulated by adversaries. Video is key to seeing and identifying threats, opportunities and obstacles, but the only way to get the video from the sensor to the observer is radio. The challenges facing today’s RF systems are three-fold: the need to avoid being observed, intercepted or jammed.
The U.S. Air Force dogma that has been in use since the 1950s of Observe, Orient, Decide, Act (OODA) is just as applicable today as it was during the Cold War. If you can get inside your adversary’s decision-cycle loop, you can win. Maximum situational awareness hinges on the number of sensors you can access to drive intelligence on the ground and in the sky.
The U.S. has enjoyed the sensor advantage over the last two decades, fighting wars in Iraq and Afghanistan. However, adversaries have quickly advanced their capabilities. As witnessed in Ukraine, Russia’s jamming of tactical radio communications over the airwaves has hurt Ukrainian defenses and disrupted tens of thousands of commercial flights1 because of interference with the GPS navigational systems of planes in European air space.
Adversarial radio signals are overwhelming communication links between drones and troops. This is causing difficulties in locating targets and tricking guided weapons, reports the New York Times. In an article,2 they quote a senior fellow at the Hudson Institute think tank as saying, “Electronic warfare has impacted the fighting in Ukraine as much as weather and terrain.”
Operational Constraints at the Tactical Edge
Digital communications-over-RF at the tactical edge faces many constraints today. These range from the need for low power consumption to limited CPU and RAM to constrained and congested bandwidth. Deployed troops rely on radios to communicate their position and coordinate their operations but often face issues of limited battery power and connectivity challenges.
These issues are compounded by cybersecurity threats, especially the looming threat of quantum computing and hybrid quantum plus AI capabilities. Understanding this latest threat requires first understanding the evolution of quantum technologies. In the 1990s, Nobel Prize-winning MIT mathematician Peter Shor developed what is now called Shor’s Algorithm, which showed that a quantum computer could efficiently factor prime numbers well beyond the capability of a classic computer. At the time, his idea was theoretical. However, once realized, Shor’s Algorithm gives the world a pathway to break current asymmetric encryption because it is based on the prime factorization of very large numbers. A sufficiently capable quantum computer using Shor’s Algorithm would be able to break asymmetric encryption almost instantaneously.
This means that traditional encrypted communication networks and legacy encryption methods like the RSA 2048 and Elliptic-curve cryptography (ECC), considered the gold standard as the U.S. government’s recognized encryption methods, are no longer sufficient on their own. Quantum advances are moving much faster than anyone guessed. Leading industry sources, including Gartner Group, Ernst & Young and Cloud Security Alliance, predict that quantum will overtake existing encryption methods this decade.
In the last two years, with the surge in AI and machine learning (ML), quantum experts have pointed out that using ML could lower the amount of quantum computing power needed to break encryption. That is why combining quantum with AI could make breaking current asymmetric encryption a reality much sooner than anticipated. AI runs on classic GPUs, while other calculations are run on a quantum processor. This hybrid combination accelerates the time window when an effective attack on this type of encryption will be possible.
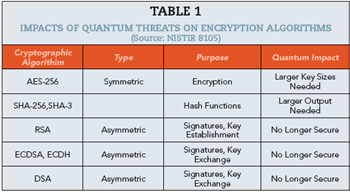
For decades, the quantum threat to encryption was presumed to be primarily related to asymmetric encryption. However, a recent IBM research paper3 suggests that AI running on a quantum computer could also attack symmetric encryption, such as the Advanced Encryption Standard (AES-256). An accelerated path to break asymmetric encryption means bad actors can intercept and interpret digital communications transmitted over RF while also opening the door to the possibility of injecting deep fakes and flooding the airwaves with noise. Deep fakes already threaten the authenticity of video content as commonly seen on the internet today. Even before a quantum or quantum/AI hybrid attack is successful, battlefield compromises of radio communications using legacy encryption have been reported.4 A report by the Royal United Services Institute for Defence and Security Studies on Russian tactics in Ukraine found that Russia was able to preemptively warn its units of an artillery strike based on Ukrainian troops calling in a fire mission after decrypting transmissions coming from Motorola radios that featured 256-bit encryption in near real-time. Such attacks are not targeted at the radio signals themselves but at the payloads that the radio waves are carrying. Even microwave transmissions, which frequently are limited to narrow-beam point-to-point connections, are still vulnerable since there can be beam spread. Table 1 shows the challenges that quantum computing poses for classic encryption algorithms.
Why the Quantum/AI Threat Matters to Military RF Users
RF communications, the lifeblood of tactical warfare, is at risk from quantum/AI threats. The U.S. has 500,000 military radios that use current classic, symmetric encryption that would all be vulnerable to this compromise. In addition to handheld applications, radios operate in ground vehicles and on military aircraft.
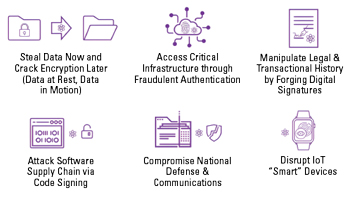
Figure 1 Potential threats from quantum computing/AI.
The quantum/AI threat extends to all devices that touch the public internet, including mobile phones and computers in the Department of Defense. To appreciate the scale of the threat, consider that the global digital economy is estimated at over $30 trillion.5 Quantum and AI have the potential to disrupt that economy and the trillions of online transactions occurring every day. Some of the potential areas for quantum computing-/AI-based disruption are shown in Figure 1.
Addressing security issues can drain the military’s limited resources. However, the overhead costs of protecting against the quantum threat should not hinder the military’s ability to conduct surveillance, mission coordination and reconnaissance. Electronic warfare environments demand maximum security while respecting the resource constraints of that environment, both for encryption and for video and radio data transmissions.
Addressing the Threat: New Quantum & Encoding Advances
A common question is, “How do we fight the next battle?” If we build a big fortification, the enemy will drive around it. If we construct a wall, the enemy will fly over it. Just as our allies in Ukraine have learned, technologies must be deployed now that provide immediate benefits and protection for the next emerging threat. The RF sector, along with the cryptography and encoding communities, needs to pivot to address this new threat environment. But the challenge becomes determining the best way to add a layer of protection against a near-term threat that will find its way to the battlefield while still addressing the pressing constraints of operating at the tactical edge.
Fortunately, the cybersecurity community is actively researching and developing new encryption methods to resist quantum computing attacks. The U.S. National Institute of Standards and Technology (NIST) is executing a process to standardize new post-quantum cryptographic algorithms (PQCs).6 These algorithms are designed to secure data against the capabilities of future quantum computers.
Fighting Quantum with Quantum
The best approach is to fight quantum with quantum. There are new mathematical approaches from companies like Quantropi that continue to advance the science to find solutions that provide security against these new attacks. However, these approaches must also balance the needs of RF communications in the current battlefield environment.
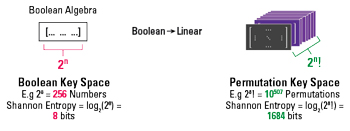
Figure 2 Permutation groups: key space and Shannon entropy expansion vs. Boolean.
In cryptography, a perfect form of encryption is called a one-time pad, where the secret is as big as the data and it only gets used one time. This scenario is called “perfectly secret.” Quantropi’s encryption is based on a permutation group that is constructed from quantum gates, which make up a “quantum permutation pad” or the quantum equivalent of a one-time pad, which achieves perfect secrecy. The company then represents this quantum permutation group mathematically. Once this mathematical expression is derived, it can be translated into computer code that will run on a “classic” CPU. This holy grail of encryption can then be used to protect against symmetric attacks and can be further leveraged to strengthen asymmetric algorithms. Figure 2 introduces the concepts of key spaces and shows the big improvement in Shannon entropy that comes from the permutation group concept just described.
Emerging Success: Post-Quantum-Protected Radios
An example of tactical capabilities receiving a post-quantum boost can be found with the Ukraine-based tactical radio supplier, Himera. Himera and its U.S. distributor, Reticulate Micro, recently unveiled the company’s G1 Pro. This is their newest lightweight and low-power radio and it comes integrated with post-quantum symmetric encryption from Quantropi.
These new capabilities represent an impressive leap from the first-generation voice-only radio, already widely deployed in the Ukraine defense forces and proven effective against Russian jamming. The G1 Pro incorporates quantum security to future-proof the radio against the looming quantum/AI threat. It also offers enhanced frequency hopping as an additional defense mechanism. The new radio offers standard AES with a 256-bit cryptographic key and Quantropi QEEP quantum symmetric cryptography with a stronger 1024-bit key. In addition, the quantum algorithm running in the radio uses 80 percent less battery power. It also decreases encryption overhead by 80 percent, leaving more room to maximize data transmission rates. Figure 3 shows the improvement in data transfer rates that the QEEP quantum symmetric cryptography produces versus standard AES-256 and AES-256-NI hardware-accelerated methods.
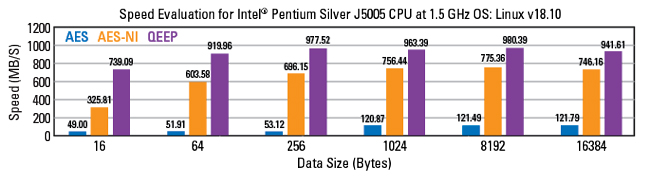
Figure 3 Data transmission rate comparison.
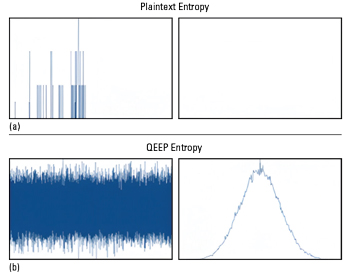
Figure 4 Plaintext entropy before QEEP encryption (a) and entropy after QEEP encryption (b).
In cryptography, plaintext refers to unencrypted, readable information input into an encryption algorithm while ciphertext refers to the output of the algorithm that has been encrypted and rendered undecipherable. As mentioned previously, entropy measures the randomness and uncertainty in a set of data. Higher levels of uncertainty and randomness of ciphertext indicate more complete security and the inability for hackers and adversaries to learn anything about the original plaintext. Figure 4a shows a plaintext signal with a very low entropy value of 5.827504/16 bits, meaning the signal is easily interpreted. Figure 4b shows that the entropy for the same plaintext signal has increased to 15.999077/16 bits after the application of QEEP encryption, making this an effectively impossible signal for adversaries and other unintended recipients to decode.
Future: Encrypting the Transport Layer
Current advances in this area are focused on data-level quantum protection on a device-by-device or application-by-application basis. A promising area of emerging research looks at bringing post-quantum protection to the physical transport layer. Focusing on the transmission itself would protect anything that is broadcast. This would make everything inherently secure. McGill University in Montreal, Quebec, is leading this research with industry partners such as Quantropi. The initial focus of this research is on photonic communications and applying quantum permutations to phase and amplitude. Future work will be applied to the radio component of the electromagnetic spectrum.
Conclusion
Quantum and AI threats are coming to today’s contested battlespace, which is increasingly reliant on capabilities at the edge. As video and data intelligence become more accessible to warfighters on the ground, we must ensure RF systems are protected, hardened and secure. Effective quantum-based defense can serve as a powerful weapon and prevent encrypted data from being exploitable or valuable to anyone but the intended recipient.
REFERENCES
- “Russia GPS Jamming ‘Thousands Of Flights In Europe’,” TalkTV, April 23, 2024, Web: youtube.com/watch?v=iEWxSo8FnEA.
- “The Invisible War in Ukraine Being Fought Over Radio Waves,” The New York Times, November 19, 2023, Web: nytimes.com/2023/11/19/technology/russia-ukraine-electronic-warfare-drone-signals.html.
- D. R. Campbell, D. W. Diffie and C. Robinson, “Advancements in Quantum Computing and AI May Impact PQC Migration Timelines,” Preprints, 2024, Web: preprints.org/manuscript/202402.1299/v1.
- J. Watling and N. Reynolds, “Meatgrinder: Russian Tactics in the Second Year of Its Invasion of Ukraine,” Royal United Services Institute for Defence and Security Studies, May 19, 2023, Web: static.rusi.org/403-SR-Russian-Tactics-web-final.pdf.
- UNCTAD, “Digital Economy Report 2024,” Web: unctad.org/publication/digital-economy-report-2024#:~:text=New%20data%20from%2043%20countries,digital%20economy%20is%20resource%20intensive.
- “Post-Quantum Cryptography Standardization,” NIST, Web: csrc.nist.gov/projects/post-quantum-cryptography/post-quantum-cryptography-standardization.

