PROTEANTECS UCT-BASED SUPPLY CHAIN SECURITY
Due to inherent process variation, especially in advanced FinFET nodes, each transistor in an IC will manifest a slight variation of its basic electrical parameters even when it is manufactured using the same template. These variations apply to electrical characteristics like threshold voltage, on current and off current. The same is also true for the resistance and capacitance of the conductors inside the chip.
These device parameters represent the DNA of an IC. If a large enough set of such parameters is analyzed, the unique DNA of the chip can be extracted and then used as a PUF. Not only is every IC different, but even more significantly, every wafer, lot and foundry is different. By collecting large manufacturing data sets and by using big data and machine learning (ML) techniques, the signature of the IC can be used to map it back to its original wafer, loT or foundry.
proteanTecs has introduced UCT as a method for collecting large sets of parametric measurements from each IC with supplementary pre-silicon simulations. Proteus, a ML-enabled cloud-based data analytics platform fuses and infers the UCT data and provides a comprehensive, holistic and secured solution for end-to-end supply chain security. Along with counterfeit detection and prevention. Proteus delivers values that are tightly related to the DNA, or the personality, of each unique device. Figure 2 shows a top-level visualization of supply chain security in a system utilizing UCT.
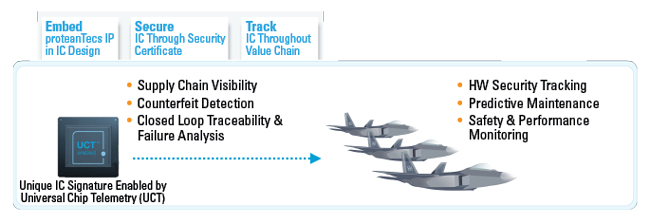
Figure 2 Supply chain security through on-chip visibility and data analytics.
Introduction to UCT
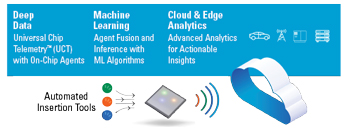
Figure 3 Proteus provides a holistic deep data solution based on UCT.
UCT is based on a collection of agents that are small monitors embedded inside an IC during the design process. These agents collect vital parametric information while the IC is tested or used in a system in fully operational mode. UCT-generated data is then loaded into Proteus, a cloud-based data analytics platform, where the data from the entire fleet of chips and systems is analyzed to produce vital insights for the design teams, production groups and fleet operators. These insights help optimize the chip and system performance and reliability during characterization, qualification, high volume manufacturing and in field use. They also provide alerts on faults before they become failures for predictive maintenance. The features of the Proteus platform, along with its integration with UCT are shown in the diagram of Figure 3.
UCT Agents
UCT agents are on-chip monitors, specifically designed for data analytics. With that in mind, the data they collect is pre-processed inside the chip and then aggregated and packed for extraction and loading into external cloud software. The agents are extremely small, spread in numbers across the chip and complement each other with the data they collect. They can be used continuously or on demand and can operate in the background while the chip is in full operational mode. They do not require a special test mode or test firmware to operate them. An overview of this UCT agent concept is shown in Figure 4.
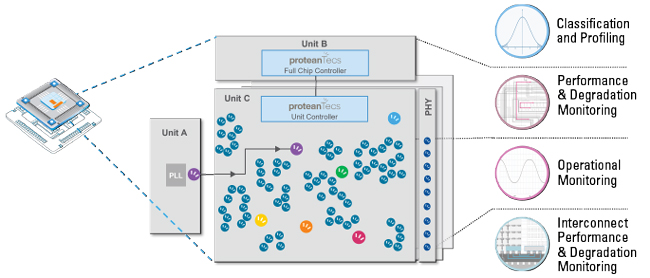
Figure 4 Four UCT agent categories.
The UCT agents are divided into four categories:
Classification and Profiling Agents collect information related to the behavior of the chip’s building elements: its basic transistors, standard cells and conductors. They are constructed to be sensitive to the different device parameters and can map a chip or a sub-chip to the closest matching process corner, Monte-Carlo simulation point and RC model. They provide fine-grain visibility of the full distribution at every stage and determine if the issue is by design or a product of process variation.
Performance and Performance Degradation Agents are placed at the end of many timing paths and continuously track the remaining timing margin to the target capture clock frequency. They can be used to pinpoint critical path timing issues as well as track their degradation over time.
Operational Agents provide deep visibility of system, software and environmental issues, as seen from the chip, as well as diagnostics as to the root cause of problems. They track changes in the DC voltage and temperature across the die as well as information related to the clock jitter, power supply noise and workload. Their information can be used to explain timing issues detected by the performance and degradation agents as well as understand the system environment in which the chip is assembled.
Interconnect Performance and Degradation Agents are located inside a high bandwidth die-to-die interface and are capable of continuously detecting the signal integrity and performance of the critical chip interfaces.
Proteus Data Analytics Cloud Platform
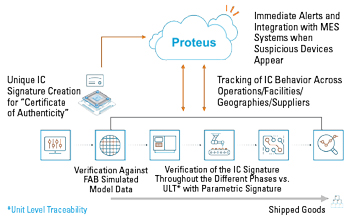
Figure 5 Signature creation and tracking across the supply chain.
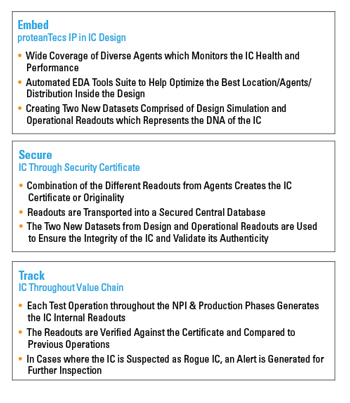
Figure 6 Embed, Secure and Track details.
The data collected from the embedded UCT agents as well as information available from other on-chip or off-chip sensors, test results from ATE, environmental and machine conditions and additional data sources are loaded into the Proteus cloud platform for deep data analytics. This highly scalable and secure platform uses ML and dedicated algorithms to process the data and fuse information from various sources, along with the entire fleet of chips and systems. The output from this information is meaningful, useful insights and alerts through a set of pre-configured dashboards. The Proteus platform also offers an open environment for customized algorithm and analytics development.
Proteus UCT-Based Supply Chain Security and Counterfeit Detection
The solution is based on three primary elements:
- Embed: Using the proteanTecs agent integration tools, each design is analyzed and a recommended set of agents are inserted to provide optimal coverage for this specific product and technology. A comprehensive set of simulations are then performed to create the baseline or the expected behavior of these agents using the target manufacturing process parameters.
- Secure: UCT data from each unit is extracted at the first test station, as early as in the wafer sort process. The Proteus Supply Chain Security module is used to calculate and assign a unique signature for each unit and store it in its secured database. At this phase, alerts can be issued for devices that seem to originate from suspected sources. These alerts may be triggered in several ways. For example, if the performance is different from the simulations, this may represent an older design revision. An alert will occur if the data does not match the intended manufacturing process models. If the data shows a significant variation from the rest of the population, this may represent counterfeit manufacturing sources or changes in the production process. These alerts are not necessarily catastrophic. If the data source that triggers an alert is deemed legitimate, the calculated signature is stored in the secured database.
- Track: At every tracking station along the supply chain, UCT data is extracted to compare and monitor the same device across its lifetime and to detect devices that falsely claim to be legitimate devices. At every test station, devices that are found to be defective, underperforming, showing signs of aging or wear-out or do not meet quality standards are marked accordingly in the secure database of this product. Tracking and continuously updating the cloud-based secure database identifies devices that were previously considered legitimate but were discarded somewhere along the supply chain. These devices may have failed test or quality requirements, they may be devices that did not meet specific binning criteria or they may be used or recycled devices.
The conceptual implementation for the supply chain is shown in Figure 5. Figure 6 gives additional details on the primary elements of the Proteus platform.
Summary
Proteus deep data analytics based on UCT provides an innovative approach to supply chain security and counterfeit detection. By generating and collecting a large set of parametric measurements from each chip and uploading them to a ML-enabled, cloud-based analytics platform, a comprehensive and secured method of detection can be achieved. This allows for continuous and intrinsic tracking of ICs through the supply chain to allow for device authentication, validation and supply chain integrity. The combination of the hardware of the UCT agents, coupled with the software of the Proteus platform makes a compelling solution for defense and commercial entities concerned with counterfeit parts and supply chain security.
References
- U. Guin, K. Huang, D. DiMase, J. M. Carulli, M. Tehranipoor and Y. Makris, “Counterfeit Integrated Circuits: A Rising Threat in the Global Semiconductor Supply Chain” Proceedings of the IEEE, Vol. 102, No. 8, August 2014, pp. 1207-1228.
- “Measuring the Magnitude of Global Counterfeiting. Creation of a Contemporary Global Measure of Physical Counterfeiting,” GIPC, U.S Chamber of Commerce, Web: www.uschamber.com.
- B. T. Horvath, “Not All Parts Are Created Equal. The Impact of Counterfeit Parts in the Air Force Supply Chain,” Air War College, Air University, April 2017.
- “Rapid Assured Microelectronics Prototypes - Commercial (RAMP-C),” NSTXL, August 2021.
- “Rapid Assured Microelectronics Prototypes using Advanced Commercial Capabilities (RAMP) Project” DOD Research & Engineering, USD(R&E), (cto.mil).
- A. Malik, “Intel Inks Deal with Department of Defense to Support Domestic Chip-building Ecosystem,” August 2021, Web: www.techcrunch.com.
- G.J. Schrijen, “Basics of SRAM PUF and How to Deploy It for IoT Security,” March 2021, Web: www.embedded.com.
- 8.K. Vaidyanathan, B. P. Das and L. Pileggi, “Detecting Reliability Attacks During Split Fabrication using Test-only BEOL Stack,” 51st ACM/EDAC/IEEE Design Automation Conference (DAC), 2014, pp. 1–6.
