There is good news for those thinking about adding wireless communications to their industrial, scientific, or medical (ISM) application. A variety of low power, low cost radio ASSPs are available that can provide wireless features specifically for ISM applications. Fortunately, you do not need to be a communications specialist to add a radio to your application, but a basic understanding of how a radio operates will help avoid implementation problems.
Radio ASSP data sheets offer both proprietary and open-standard protocols, and will contain specifications that can be rather cryptic to those unfamiliar with wireless communications. This article explains the terms and how they relate to the application.
Wireless communications is all about the transmission of data - usually digital data (that is, ones and zeroes) - from a transmitter to a receiver without the need for a physical connection. Most radio ICs are transceivers, which means the ASSP can both transmit and receive data. A transceiver is often paired with a simple microprocessor or other support circuitry that can direct the flow of information as well as perform additional services, such as error checking.

In the simple radio shown in Figure 1 , the analog data from a sensor measurement is first digitized. A microcontroller then adds some error detection code and formats the data for transmission. The digital data is sent to the transceiver, encoded onto an RF signal and broadcast by the transmitter, detected by the receiver and finally decoded back into digital data.
Common ISM Radio Requirements
ISM radios are usually driven by two primary requirements. First, they must consume very little power so that they can last on battery power for months or years. Second, ISM radios must have a low system cost with simple design and few external components so that they can be added to other low cost small-size components, such as sensors.
ISM applications are usually indoors and have a relatively short range over which data must be transmitted. In addition, they only need to transmit a small amount of data on an infrequent basis. A short data range means that the radio design can be kept simple and the transmitter power can be kept low. The infrequent data transfer means that ISM radios can spend a large portion of their time asleep. Both of these requirements help to greatly conserve power.
Of course, the requirements of your wireless system will go beyond low power and low cost. Table 1 lists several additional requirements you should consider when reviewing possible wireless system architectures.
|
Table 1 | ||
|
Requirement |
Questions |
Comment |
|
Environment |
Is the indoor/outdoor environment crowded with obstacles? Do other transmitters exist? |
A noise environment requires robust data error detection |
|
Data rate |
How much data must be transmitted? How often? How fast? |
Higher data rates consume more power, require more sophisticated designs |
|
Data range |
How far apart will the transmitter and receiver be? |
Longer ranges require more transmit power and sensitive receivers |
|
Power consumption |
What type of batteries will be used? How many? |
Power consumption is dependent on many factors including transmitter power, carrier frequency and data rate |
|
Topology |
Point-to-point or point-to-multipoint? |
Point-to-point systems are easier, cheaper to develop |
|
Speed and latency |
How time sensitive is the data? |
Overhead associated with error detection and correction increases latency |
|
Interoperability |
Does the radio interface with other radios? |
If yes, likely requires an open- standard protocol |
|
Host intelligence |
How much data processing capability is required? |
Overhead associated with error detection and correction increases processing power |
|
Size and system cost |
How much room is available for antennas and external components? |
Portable applications have little room for external components |
|
Security |
How secure does the transmitted data need to be? |
Encryption codes can be added by the host intelligence |
Selecting a Frequency Band
Both the US Government and the European Union govern the kind of information that can be transmitted at a given frequency and at a given transmitter power. Several licensed frequency bands exist specifically for medical or industrial applications. However, most low cost applications operate in one of the few unlicensed frequency bands to avoid the need to obtain a frequency license from a regulatory agency.

Low power transceiver ICs usually operate between 300 MHz and 1 GHz. The frequency spectrum (see Figure 2 ) between these limits contains many bands where both licensed and unlicensed medical and industrial equipment can operate. Table 2 shows the common unlicensed frequency bands used in North America and Europe that are suitable for ISM applications.
|
Table 2 | |||
|
Frequency (MHz) |
Geographic Region |
Band |
Regulation |
|
433.05 to 434.79 |
Europe |
general telemetry |
EN 300 220 |
|
868.00 to 870.00 |
Europe |
general telemetry |
EN 300 220 |
|
902.00 to 928.00 |
N. America, Australia, S. America |
915 MHz ISM band |
FCC 15.247 |
|
2400.00 to 2483.50 |
Europe |
2.4 GHz ISM band |
ETS 300 328 |
|
2400.00 to 2500.00 |
N. America |
2.4 GHz ISM band |
FCC 15.247 |
|
5650.00 to 5925.00 |
N. America |
5.7 GHz ISM band |
FCC 15.247 |
Selecting a Transmission Protocol
Transmission protocols define the way data is to be encoded, transmitted, received and decoded. Protocols also define any error-correction methods as well as techniques to minimize interference and distortion. Protocols are usually optimized for the given application to reduce the overhead associated with error-correction, and thereby obtain lower cost and lower power operation.
Open-standard protocols and proprietary protocols exist for all of the ISM bands. If interoperability between transceivers from different manufacturers is a concern, an open-standard protocol must be considered. Open-standard protocols can also allow for a complex networking of transmitters and receivers such as those operating in a mesh-type of network. However, standard protocols give up some flexibility and add considerable overhead to obtain compatibility and interoperability.

Figure 3 maps several open standards against the unlicensed frequency bands. The low data rates typical of ISM applications mean that current wireless local area network (WLAN) and wireless personal area network (WPAN) open standards such as IEEE 802.11b/ a/g and Bluetooth are overkill because they were developed to address high speed data transmission needs.
Proprietary protocols may be offered by one or more ASSP suppliers, and can often fit a given application better than a standard. When interoperability between different device manufacturers is not a concern, a proprietary protocol can offer more flexibility, provide lower power operation and can be cheaper.
A few considerations should be taken into account when choosing a protocol and an associated unlicensed frequency band. These considerations include:
- Geographic location: The various ISM frequency bands used around the world do not necessarily coincide. The 2.4 GHz band is generally available in most locations but may be restricted depending on the country. Other lower frequency bands are restricted to a geographic location.
- Interoperability: If the application requires that devices from several manufacturers work together, than a specific communications standard must be used. That standard will define the frequency range. The newly adopted IEEE 802.15.4 standard, commonly known as "Zigbee," addresses the 868 MHz, 902 to 928 MHz and 2.4 GHz ISM bands, and ensures interoperability between devices.
- Interference: Multiple wireless standards often coexist in these unlicensed frequency bands. For example, 900 MHz cordless phones operate in the 902 to 928 MHz band. Since the 2.4 GHz band is useable in most locations, it is a popular choice for a variety of wireless communications protocols. Microwave oven operation can also plague that band.
Low data rate radios can usually host both the protocol and application control in a simple eight-bit microcontroller. Typical applications use only 4 to 30 kbytes of code and less than 300 to 4000 bytes of RAM, depending on whether the host is a full-function controller or a subordinate reduced-function device.
By comparison, more sophisticated radios such as Bluetooth require a dedicated core to manage the baseband protocol stack and a separate host device to manage the Logical Link Control and Adaptation protocol, RFCOMM, protocol interfaces and applications. About 100 to 200 kbytes of code and about 150 kbytes of ROM for a full software stack may be required.
Topology
Wireless receivers and transmitters are often arranged in a "star" configuration, where a centrally located transceiver communicates with one remote location (a point-to-point topology) or with several locations (a point-to-multipoint topology), as shown in Figure 4 .

In a point-to-point architecture, only one transmitter and receiver pair is communicating at any given time on a specific carrier frequency. The central node takes the role of a master coordinator, while the remote location is a subordinate. Point-to-point communications can be simplex (one way only), half duplex (first one direction and then the other, sequentially) and full duplex (simultaneous communication in both directions).
Networks that are more complex may have multiple transmitters and receivers that can communicate with one another as peers. Within a network, one of the central nodes is designated as a coordinator tasked with waking up other subordinate devices on the network out of a low current sleep-mode just before data is to be transmitted. Coordinators can also talk to one another as peers.
Mesh networks can allow wireless devices to talk indirectly to one another even when the two devices cannot see each other. A transmitting device can pass data to its neighbor, which in turn can pass data onto its next neighbor, and so on. In this way, a mesh network can be used over a far-flung network, say between the top and bottom floor in a high rise building.
Open-standard vs. Proprietary Protocols
An understanding of the tradeoffs between open standards and proprietary protocols can be developed by comparing two similar radio transceivers that operate in the same 868 MHz (EU) and 902 MHz (US) unlicensed ISM bands.
Appendix A shows how two different transceiver designs operating in the same frequency bands address the wireless system requirements noted previously. Transceiver A follows a more complex open-standard protocol IEEE 802.15.4, while Transceiver B follows a simpler but proprietary protocol.
Environmental Requirements
In an ISM environment, data transmissions through a wire or along a circuit board trace are always vulnerable to interfering signals, coupled noise, electromagnetic interference, and noisy or shifting power and ground planes. A common method of overcoming transmission problems is to use the digital data to modulate a much higher frequency signal, called a carrier signal. Carrier modulation techniques convert the digital signals into frequencies that are inherently more noise-immune. Since the shifting carrier signal is an AC signal with no ground reference, the carrier signal is not affected by unstable or noisy ground planes. The carrier frequencies can be tuned to avoid electrical noise and the receiver circuits designed to reject out-of-band noise. The receiver can also be designed to reliably detect very small changes in frequency that can yield long data ranges with very little power.
Carrier Modulation Techniques
There are a number of techniques that can encode digital data by varying either the amplitude, frequency, or phase of a carrier signal. Examples of each are shown in Figure 5 .

- Frequency shift key (FSK) modulation uses two different carrier frequencies to represent the logic high and logic low of digital data.
- Amplitude shift key (ASK) modulation uses one frequency but varies the amplitude of the RF carrier to represent the logic high and logic low of digital data. A variation of ASK is called on/off shift key (OOSK) modulation, where one of the two amplitudes is zero. The OOSK signal is a series of alternating frequency bursts and quiet periods representing the logic high and logic low of digital data. ASK is not as noise-immune as FSK but is often easier to implement and detect.
- Phase shift key (PSK) modulation encodes the digital data by altering the phase of the carrier frequency. Biphase shift key (BPSK) modulation shifts the phase of the RF carrier by 180° in accordance with a digital bit stream. The receiver performs a differential coherent detection process whereby the phase of each bit is compared to the phase of the preceding bit.
From the data, it can be seen that Transmitter A uses the BPSK modulation technique, while Transmitter B uses an OOSK modulation technique. BPSK is more difficult to implement but can offer up to a 6 dB advantage in signal-to-noise ratio over OOSK for a given carrier level.

Multipath Propagation Problems
Now that the digital data has been encoded as an RF carrier signal, new environmental problems can affect the data signal. Multipath propagation occurs when an RF signal takes different paths when propagating from a transmitter to a receiver. While the signal is enroute, walls, chairs, desks and other items get in the way and cause the signal to bounce in different directions. A portion of the signal may go directly to the destination, and another part may bounce from a chair to the ceiling, and then to the destination, as illustrated in Figure 6 . Therefore, some of the signal will encounter delay and travel longer paths to the receiver.
Multipath delay causes the information symbols represented in a radio signal to overlap, which confuses the receiver. This is often referred to as intersymbol interference (ISI). Because the shape of the signal conveys the information being transmitted, the receiver will make mistakes when demodulating the signal's information. If the delays are great enough, bit errors will occur. The receiver won't be able to distinguish the symbols and interpret the corresponding bits correctly.
Radio Interference Problems
Since the unlicensed bands permit the use of any type of radio within the guidelines established by the governmental regulatory agencies, the bands are becoming increasingly crowded with wireless information from many different sources. Cordless and cellular phones and microwave ovens are common devices operating in unlicensed bands that can corrupt data signals in the same band. Airborne radiolocation systems also share these bands.
RF interference occurs when these types of unwanted RF signals transmit at the same carrier frequency as a legitimate signal, causing an interruption or corruption of the legitimate signal. Corrupted legitimate signals arrive with errors, missing bits, or not at all, and the receiver cannot recover the data. Depending on the sophistication of the receiver/transmitter set, the transmitter may be asked to resend the data, which in turn adds overhead to the network and causes delays.
Multipath and Interference Reduction Techniques
Depending on the application, radio interference may not be as big a concern if the environment is relatively quiet. However, indoor short-range radios in the unlicensed ISM bands must be able to account for multipath problems.
Both active and passive techniques are used to account for multipath fading. Passive techniques are generally much lower in cost and rely on diversity antenna systems, which is the use of two antennas for each radio to increase the odds of receiving a better signal on either of the antennas.

Diversity antennas have a physical separation from both the radio and each other to ensure that one of the antennas will encounter less multipath propagation effects than the other antenna. An example is shown in Figure 7 . The receiver uses two separate receiver paths to filter the signal and then decides which signal is the best choice for demodulation.
Active techniques employ spread spectrum technology to address multipath fading and RF interference. Two commonly used techniques are direct-sequence spread spectrum (DSSS) and frequency hopping spread spectrum (FHSS).
DSSS mixes a data signal with a constantly changing pseudo-random noise signal that spreads a continuous data signal over a wide range of frequencies. This leaves enough room for lower frequency elements of the DSSS signal to reflect off obstacles much differently than the higher frequency elements of the signal. Transceiver A employs DSSS.
FHSS transmits an intermittent data signal for a short period at one frequency and then hops to other frequencies in a pseudo-random pattern. FHSS avoids interference from other radios by hopping on narrow channels over a wide range of frequencies, transmitting on strong, clear channels and avoiding noisy or faded ones.
Frequency hopping is generally regarded as having better noise immunity than DSSS, although the data rate is lower. Bluetooth radios commonly use frequency-hopping techniques.
Data Integrity Checks
Error detection and correction are also important in mitigating the effects of interference and multipath fading. The receiver checks for the presence of errors through an error checking process. Basic designs use a simple checksum, but a cyclic redundancy code (CRC) check is necessary for more reliable data transmission.
Transceiver A adds a CRC to every data packet that is sent. A data packet containing an error will not compute correctly. The drawback of added overhead is more than offset by ensuring the received data is accurate. For low data rate radios, a CRC of 16 bits is adequate; for high data rate radios, a CRC of 24 bits is ideal.
In a point-to-point topology, a simple handshake protocol between the receiver and transmitter known as automatic retransmit request (ARQ) requires the receiver to send an acknowledgment if data has been received with no errors. If an acknowledgment is not received by the transmitter, the transmitter tries again to resend the data.
With complex network topologies, such as point-to-multipoint or peer-to-peer topologies, the protocol must provide for one receiver to accommodate multiple transmitters broadcasting at the same time. The primary scheme is called Carrier Sense Multiple Access with Collision Detection (CSMA/CD). CSMA/CD is a set of standard rules that determine how network devices should respond when two devices attempt to use the same channel. The handshaking process between receiver and transmitter is similar to ARQ. After detecting a collision, a transmitter waits a random delay time and then attempts to re-transmit the data. If the transmitter detects a collision again, the device waits twice as long to try to re-transmit the message. This is known as exponential back off.
Because of data retransmissions, the data rate throughput is slow when multipath is significant. The reduction in throughput depends on the environment. Radio signals in homes and offices may encounter 50 ns of multipath delay. Metal machinery and racks in a plant, however, provide a lot of reflective surfaces for RF signals to bounce from and take erratic paths. Signal delay in a manufacturing plant could be as high as 300 ns. Be wary of multipath problems in warehouses, processing plants and other areas full of irregular, metal obstacles.
Data Rate Estimation
The data rate of your wireless network can be estimated based on how much data must be transmitted, and the additional overhead is required by the chosen protocol to perform error detection and correction. As noted earlier, multipath and interference effects will cause the occasional transmission to be retransmitted due to errors in the data. A 90 percent success rate can be used as a conservative estimate for a well-designed system, which means that 10 percent of the transmissions must be resent.
For a point-to-point system, the data rate can be expressed as
Data rate = [(PD + AO + PO) x (1 + retry%)]/transmission time
where
PD = payload data in bits
AO = application overhead in bits per payload transmission
PO = radio overhead in bits per payload transmission
retry% = retry percentage
transmission time = time required to send the data
Assume a remote sensor unit is required to send 10 bytes of sensor data in response to a 2 byte transmit command within 100 ms every 10 seconds. The application uses a format consisting of a start byte, an address byte, the 10 bytes of payload data and a 2 byte CRC, resulting in an application overhead of 4 bytes (start, address, CRC) or 32 bits. Assume also the protocol overhead is 64 bits and that two transmissions must take place during that 100 ms interval (transmit and receive).
The required data rate can be estimated as
Data Rate =
[transmit command]
+ [receive command] x [1+retry%]
transmission time
Data Rate =
[16 bits + 32 bits + 64 bits]
+ [80 bits + 32 bits + 64 bits] x 1.1
100 ms
Data Rate =
316.8 bits
0.1 s
Data Rate =
3168 bits/s,
or roughly 3 kbytes/second
This estimated data rate can then be compared to the data rate capabilities provided in the transceiver features. From Table 3, Transceiver A can support 20 to 40 kb/s, while Transceiver B can support from approximately 2 to 20 kb/s.
Data Range Estimation
The effective data range of a wireless network can be estimated from a simple calculation of signal power loss, an estimation of antenna gain, the height of those antennas above ground, and knowledge of the transmitter power and receiver sensitivity.
Transmit Power and Receive Sensitivity
Transmitter power refers to the energy used to broadcast a signal. It follows that the larger the transmitter power, the longer the transmitter range will be. However, the upper limits on transmitter power are driven by both regulatory and power-consumption issues.
In the 868 to 870 MHz band, the European Telecommunication Standards Institute (ETSI) allows just 100 mW (20 dBm) effective isotropic radiated power (EIRP), while the FCC permits up to 500 mW (27 dBm) in the 902 to 928 MHz band. Most other countries follow either the US or ETSI rules. Therefore, to create a product that can be used in this band worldwide, most manufacturers limit the transmit power to 100 mW.
On the power-consumption side, its important to note that even the most efficient power amplifiers have efficiencies only slightly better than 50 percent. That means transmitting 100 mW of signal requires at least 200 mW of power for the power amplifier alone.
Transceivers offset the energy consumption of the power amplifier by turning the amplifier off when no data is to be transmitted. Except in very heavy traffic point-to-point links, any one radio will rarely transmit more than 25 percent of the time. In applications with intermittent data streams, the entire transceiver can be placed in a sleep mode.
The receiver sensitivity is an indication of the level of signal strength that must be present at the receiver to correctly obtain data at a specified bit-error rate. The receiver sensitivity depends on the data rate, the carrier modulation technique and the low level environmental frequency noise. A theoretical receive sensitivity can be estimated by
Receive sensitivity = Nt + Ns + SNR + 10log10 (Data Rate)
where
Nt = thermal noise floor
Ns = system noise figure
Data Rate = rate of data transfer
SNR = minimum signal-to-noise ratio required for a given bit-error rate
The important thing to note is that a doubling of the data rate reduces the receiver sensitivity by 3 dB. Therefore, the higher the data rate, the lower the data range.
Antenna Gain
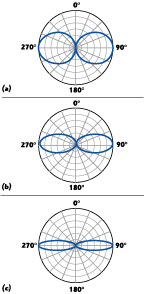
Antenna selection is guided by antenna size and cost followed by desired coverage area and gain. Antenna gain results from focusing transmitted energy into a cross-sectional area. The simplest antenna is the omni-directional dipole antenna. The ideal signal radiation pattern of a dipole antenna in free space would have a donut shape, as shown in Figure 8a .
An antenna cannot create power but it can focus energy into a more useful pattern. For example, by doubling the radiated transmitter power in the direction of an intended receiver, as shown in Figure 8b , the antenna can be said to provide a 3 dB "gain." Doubling the radiated energy density yet again yields a 6 dB gain, as seen in Figure 8c .
Limiting the radiated energy to a portion of the donut pattern increases signal intensity in the focal area, as illustrated in Figure 9 . The smaller the coverage area, the higher the antenna gain.
In indoor applications, directional antennas can provide better performance than omni-directional antennas. The performance is due not to energy concentration but instead to a reduction in the off-axis dispersion that reduces multipath cancellation effects.

The sum of the antenna gain and the transmit power may be referred to as the effective isotropic radiated power, or EIRP. For example, regulatory rules may limit radiated power to 30 dBm EIRP in a given band. That example power level could be obtained by adding a 6 dBi antenna to a 24 dBm transmitter or by using an 18 dBi antenna with a 12 dBm transmitter.
Signal Power Loss
Data range is the most difficult parameter to estimate simply because of all of the multipath effects that occur in indoor environments. If the data range is not adequate, however, the radio may not work or may require additional transmitters and receivers.
As a first step to estimating data range, a parameter known as free space loss must be estimated. Path loss is the estimated loss of signal power through the "free space" between transmitter and receiver.
The Plane Earth propagation model is commonly used to calculate signal power loss. The model reflects the average signal attenuation over distance for a stationary transmitter and receiver with a clear line-of-sight.
For radios in the UHF bands between 200 and 5000 MHz, the signal loss may be roughly estimated as
LossPE = 10 log (D4/HT2 x HR2)
where
D = distance between transmit and receive antennas
HT = height of the transmit antenna above ground
HR = height of the receive antenna above ground
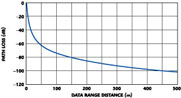
It is assumed that D is much greater than H for either antenna. For two antennas 1.5 m above ground, the Plane Earth model estimates the signal loss over distance, as shown in Figure 10 . For a signal to propagate from the transmitter to the receiver, the sum of the transmitter power, the receive sensitivity and the antenna gains must be larger than the estimated signal power loss. The RF link budget can be expressed as
LB = PT - SR + GT + GR
where
LB = link budget
PT = transmitter power
SR = receiver sensitivity
GT = transmit antenna gain
GR = receive antenna gain
Note that the link budget had better be greater than or equal to the signal path loss or the system will not function.
Data Range Calculation
Finally, all the values are available to provide a quick data range estimation. Using the RF link budget and the equation for the signal power loss, the estimated data range distance can be calculated as

Consider an RF system using Transceiver B operating at 915 MHz. From Appendix A, the transceiver has a transmit power of +6 dBm and a receiver sensitivity of -103 dBm.
Assume the transmit and receive antennas have 0 dBi of gain. The link budget would add up to 6 - (-103) + 0 + 0 = 109 dB.
Interior radio practice generally assumes 15 to 20 dB of fade margin, which provides for differences in multipath, shadows, reflections, system losses and other nonidealities. A 15 dB fade margin yields approximately 94 dB of usable link budget, assuming each antenna is about 1 m off the ground and solving for the distance yields an estimated maximum line-of-sight range of approximately 223 m.
Remember that as the Data Rate doubles the Receiver Sensitivity drops 3 dB due to increased signal-to-noise requirements, which in turn reduces the effective data range. To ensure reliable system operation in a variety of indoor locations, there is no substitute for a site survey to identify shaded areas and to determine the obtained range. These data should be used to plan RF equipment deployment.
References
1. ETSI EN 300 220-1, European Standard (Telecommunications series), V1.3.1, September 2000.
2. ETSI EN 300 328, Candidate Harmonized European Standard (Telecommunications series), V1.4.1, November 2002.
3. ETSI EN 301 839-2, Candidate Harmonized European Standard (Telecommunications series), V1.1.1, April 2002.
4. Code of Federal Regulations, Title 47 Telecommunication, Part 15, National Archives and Records Administration, Washington, DC, August 20, 2002.
5. B. Sklar, Digital Communications, Fundamentals and Applications , Prentice Hall, Englewood Cliffs, NJ 1998.
6. E. Callaway, et al., "Home Networking with IEEE 802.15.4: A Developing Standard for Low Rate Wireless Personal Area Networks," IEEE Communications Magazine , Vol. 40, No. 8, August 2002, pp. 70-77.
7. J. Yoshida, "Group Backs Zigbee as Pervasive Wireless Spec," EETimes , November 9, 2001.
8. A. Bensky, "Range Estimation for Short-range Event Transmission Systems," RF Design , November 2002, pp. 30-39.
Carl Falcon earned his BSEE and MSEE degrees from Drexel University and his MBA from St. Joseph's University. He joined AMI Semiconductor in 1997 and currently serves as a strategic marketing manager. He is a member of the IEEE and has authored several articles on mixed-signal CMOS ASIC design and PLL-based clock generators.

