This project was started in order to develop a device that could detect concealed guns on people to protect police officers by allowing them to frisk a suspect at a distance. The original concept was to have the unit in a handheld, battery operated package. Other applications included the protection of people at schools and sporting events by preventing the infiltration of concealed weapons. The applications were expanded with the advent of terrorists to include additional threats, such as suicide bombs. Hence, the resulting product is entitled a concealed threat detector.
Background and Initiation
The motivation to embark on this project was based on the premise that objects, such as a gun, would have a radar signature that was sufficiently unique that it could be distinguishable from other objects that are normally carried by people. These normal objects are categorized as pocket clutter. To determine whether or not the premise was correct an experiment was devised that used an impulse radar. This was around 1995 when impulse and ultra-wideband radar was an emerging technology.
The initial experiment was conducted in an anechoic chamber. A person with normal pocket clutter was placed in front of an impulse generator terminated in an ultra-wideband antenna, also called an Impulse Radiating Antenna (IRA). Next to the transmitter was a receiver that was shielded from the transmitter by a septum coated with absorptive material. Therefore, the receiver would record the signal being reflected by the person under test. The received signal was recorded by a very wideband oscilloscope. This recorded a time domain waveform of the reflected signal. This test was repeated several times with two or three different people who were either armed with a gun or not.
The result showed a small, but definite increase in the reflected energy in the 1 to 2 GHz band when a gun was present versus the situation when it was not. This test was conducted and plotted several times for an armed and unarmed condition. Based on these results a privately funded venture was launched by The MacAleese Companies to develop such a product. It was quickly realized, however, that an impulse radar is awkward and expensive to produce. The development cost is also very high. Therefore, alternatives to the initial technology were sought. After evaluating various technical approaches, and associated cost to reduce this concept to practice and commercialize such a device, it was decided that the Electro Science Technologies (EST) approach had the best probability of success at the most reasonable cost. That approach was to simulate the operation of an impulse radar by using a wider pulse of many nanoseconds and stepping it across the frequency band of interest thereby creating a frequency domain waveform. That was then converted to the time domain by use of a fast Fourier transform (FFT) and later a Chirp-Z transform. This theoretically provides the same information, but in an easier to obtain form.
As the world situation changed, the emphasis shifted from the detection of concealed handguns to the detection of concealed bombs and assault rifles. This shift has been accommodated with a very high degree of success.
Approach
The EST approach was to use a frequency domain approach to collect the data instead of a time domain system. The resulting signal waveform is then converted to time domain using a Chirp-Z transform. The impulse radar transmits a pulse with a duration of several hundred picoseconds and an amplitude of many kilovolts per meter. Such a device is quite expensive, large and heavy, and has many limitations. The EST approach was to transmit a 10 nanosecond pulse at a fixed frequency, read the return in a receiver with a bandwidth of several hundred megahertz, and then take a frequency step and repeat the measurement. This can be done at several hundred frequencies to create a frequency domain response, which can then be transformed into the time domain. The impulse radar collects its data in a matter of picoseconds whereas the frequency-stepped approach requires several milliseconds. Even though this data collection time is many orders of magnitude greater, for all practical purposes it is still real time. The EST approach therefore allows a radar to be built that follows a conventional block diagram with surmountable challenges in the area of narrow pulse widths and the associated bandwidths.
The stepped frequency or spread spectrum approach also offers some additional advantages. The antennas are no longer state-of-the-art specials and the peak power levels are only a fraction of a watt for the short range that needs to be covered. Furthermore, the impulse radar was frequency band limited by the duration of the impulse. That is, the energy in an impulse drops to zero at 1/pulse width. At 80 percent of that frequency the power level is already significantly reduced. Then, to increase the frequency range of the signal, the impulse must be made narrower. The energy in the impulse is the integration of the power as a function of time. Therefore, as the pulse width narrows, the amplitude must proportionately increase in order to maintain a constant energy level.
The frequency-stepped system can scan over a wider frequency range (several gigahertz if desired) and the center frequency can be moved to any desirable band. This is very significant as the desired information may reside better at another part of the spectrum, where the impulse does not have sufficient energy to create a response. Furthermore, most of the energy transmitted by the impulse radar is in the lower frequency portion of the spectrum below 1 GHz. It was experimentally determined that there was no information, useful for the intended detection, in that part of the spectrum. It then becomes very inefficient to use this type of waveform for this application. The EST frequency scan approach corrects this situation.

The approach then was to build a frequency scanning radar. The original experiments, using the impulse radar, produced results that were a representation in the time domain that was then transformed into the frequency domain, while the frequency scanning radar produced a result that was immediately in the frequency domain. Ironically, it turned out that there is only a small amount of the desired information in a frequency domain waveform and most is extracted from the transformed time domain waveform. Thus, the waveform is transformed into a well-behaved time domain response for which accurate readings can be rendered.
Design and Evolution

Achieving a well-behaved waveform requires phase coherency of the returned signals. Phase detectors that can respond to pulses on the order of 10 nanoseconds are difficult to realize. Additionally, it became difficult to obtain modulators that could produce a 10 nanosecond pulse with a rise and fall time of less than two nanoseconds at a reasonable price with repeatable performance. As a result, the system was changed to an interrupted CW radar which greatly simplified the phase detectors along with the requirements for the high speed modulator. That also eliminated the T/R and range gate switches. The term interrupted CW is used since the time that the signal is present is long compared to the transit time of the signal to target and back.
The current system transmits an interrupted CW signal with horizontal polarization and simultaneously receives the returns from a test subject in both the vertical and horizontal polarizations. The horizontal return is referred to as the co-pol signal and the vertically polarized return is the cross-pol signal. Figure 1 shows a block diagram of the current system. It was experimentally determined that there is a huge advantage to receiving both polarity returns as many more parameters were available to establish a decision as to whether or not a person is armed. Figure 2 shows a production unit.

Being a CW system, range gating is now done mathematically. A single receiver is used to measure both polarity return signals. The input to the receiver is switched between the co- and cross-pol antennas. The antenna is made in three patch array sections. One is the horizontally polarized transmit antenna. The others are vertically and horizontally polarized receive antennas. The receiver is a conventional superhet erodyne receiver with amplitude and phase detectors. The IF section contains a variable gain feature. This is accomplished by the use of digitally controlled step attenuators. The analog outputs of these detectors are fed to the processor board where they are digitized. The co- and cross-pol values are read and stored at one frequency. The transmit oscillator is then stepped to the next frequency and phase locked. The transmission is then enabled and the readings on the return signals are then measured and stored. This process is repeated 256 times to cover the operating band of 9.50 to 10.55 GHz. At the end of 256 measurements a frequency domain waveform is created. That waveform is then transformed into a time domain waveform from which several pertinent parameters are extracted. Those values are processed in an artificial neural net, which is then able to offer a decision on whether or not the person being examined fits within the trained parameters of being “normal” or “abnormal.” If abnormal, a THREAT decision is generated. The output decision, along with a visual image of the test subject, is seen by an operator on a closed circuit TV screen. An example is shown in Figure 3. The general specifications for this system are shown in Table 1.

The usual range of operation, as determined by various users, is in the 9 to 15 foot range. However, significantly longer ranges are possible by the use of a larger patch array antenna. The current antenna produces a pattern that is approximately six feet (1.8 m) high by three feet (0.9 m) wide at a range of 12 feet (3.6 m). This provides full head-to-toe coverage of a subject. Larger people can be fully illuminated by examining them at 15 feet (4.5 m).
It should be mentioned that, except in rare cases, no single parameter provides a conclusive piece of information. Each has a trend, some of which are more definite than others. The combination and weighing of many parameters converges on a reliable decision.
The latest model uses a next level of sophistication by employing both monostatic and bistatic detection. In this configuration, at least two units are used and each makes its own monostatic measurements plus a set of bistatic measurements. The latter is accomplished by transmitting a horizontally polarized signal from the master unit and receiving the horizontal and vertical target scattering at the slave unit. Due to the detection requiring coherency, the received signals are brought from the slave to the master for processing. This system adds many more parameters that can be considered in rendering a decision on a person; hence, another improvement in accuracy. Furthermore, the bistatically received signal is a very significant aid in the detection of all shapes of shrapnel. Being that monostatic detection is used from multiple angles plus bistatic detection, it is virtually impossible to devise a shrapnel form that can avoid detection.

Figure 4 is a block diagram of the bistatic version of the Concealed Threat Detector (CTD). As shown, the signals are all derived at the master unit and brought to the slave via a cable. Then all received signals are cabled back to the master for coherent processing. Therefore, the slave unit in this configuration basically only contains a three-section antenna, some switching circuitry, amplifiers to compensate for the cable losses and a power supply to power the mentioned devices. A laser is also included to assist in the aiming of the device.
Figure 5 shows a typical physical setup using two units. An alternate setup used three units. The third unit is placed behind the subject being tested so that a simultaneous rear view is obtained. This eliminates the need for the subject to turn around. The rear unit operates fairly independently of the two front ones, as its point of view is totally different than the front units. The rear slave unit does send its information to the master so that only one compiled output is presented to the operator. The information from the rear unit is also useful for further verifying some parameters.

Applications
While the CTD can process a large amount of people sequentially, it is likely of best value in low volume situations. Such high value screening points would include:
• Embassies
• Government Buildings—mints, legislative offices, court houses, administrative offices, etc.
• Public buildings—schools, libraries, museums
• Transportation hubs—bus terminals, train stations
• Sporting events
• Border crossing points
• National monuments
• Research facilities and laboratories
The screening process is simply to have a person being checked walk into a marked test box, face the prompter monitor and put their arms out. The reason for arms out is to reveal the area under the armpit, where a weapon like a gun in a shoulder holster could be hidden from the radar by the flesh of the upper arm. The instrument detects the presence of the individual and begins the measurement process. During the process, three sets of readings are taken and the final decision is made by polling the readings and then looking at the total score. In the vast majority of cases, when a weapon or threat is present, the first two readings are conclusive. In those cases, the third reading is not taken and the results are immediately presented. This situation requires only about three seconds to complete the screening process.

The CTD is quite practical as no special portals need be set up and the small units operate well in a simple open space. This allows people to be screened prior to entering a building where generally more damage can be done by a terrorist. The operator can be remotely located since the output is presented as text over video so that the operator has a visual picture of the test subject plus the output information from the system. Figure 6 shows a typical output screen with a SAFE indication along with the individual’s score. The operator or system administrator can adjust the threshold at which the decision changes from SAFE to THREAT, and thereby adjust the system sensitivity. As shown, the person’s score is also presented so that the operator can apply some human judgment if appropriate. Otherwise the system will provide a definite decision.
Performance and Results
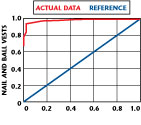
Judging the performance of such a system is not trivial. Even establishing a test plan is quite complex and must contend with many variables. One method that was suggested by the Transportation Security Administration (TSA) is the use of a graphical representation called a Receiver Operational Characteristic or ROC curve. Such a curve is shown in Figure 7. The abscissa is the false positive rate and the ordinate is the true positive (or detection) rate. The reference is a line with a slope of 1. This is equivalent to a coin toss or a 50-50 prediction. An absolutely perfect system would essentially be a point at the upper left hand corner, which represents 100% detection with 0% false alarms. Since no system is so perfect, the actual performance is shown as a curve. This system, like any other, allows for a range of sensitivities. If the sensitivity is increased, the detection rate is increased along with the false alarm rate. Therefore, there is a tradeoff between the two. Different situations can tolerate different false alarm rates. This curve shows that the Safe Zone System has a detection rate of 98% with a false alarm rate of less than 5%. This is considered to be excellent performance.
Since the operator is presented with a score or certainty factor along with the decision of the artificial intelligence, the accuracy can be further improved by applying some human judgment to the decision. That is, if a person gets a SAFE decision from the processor but their score is very close to triggering a danger level, the operator may want to examine this person again or make some visual judgment or further examination. An example might be that the body and head sizes do not seem to match indicating that there may be more than the person under the clothing. An operator could be assisted with this judgment on future models where a person’s radar cross-section is compared to the number of pixels their visual image transcends. There are many such features that can be included in future models to increase the difficulty for a terrorist to pass a screening system of this type.

The current versions of the CTD have been tested with threats that use all shapes of shrapnel and some that use no shrapnel at all. Those contained only packets of C-4 or similar explosive and even a thin layer of sheet explosive. Figure 8 shows a sample of some of the threats that have undergone detection testing with the CTD.
At the time of this writing, the system is in line to be tested and results verified by various government agencies. In anticipation of favorable test results, several hundred units have been produced with excellent repeatability. Additionally, Federal Communications Commission (FCC) approval is expected imminently.
Conclusion
A standoff concealed threat detection system has been developed and produced that is capable of detecting objects concealed under a person’s clothing that can be considered dangerous. This system operates at a low power level in X-band. The typical range of operation is on the order of 15 feet and can be extended to 100 feet or more by the use of a higher gain antenna. Accuracy and performance depend on many factors, but under normal circumstances the detection rate is in the very high 90s percentile with an associated false alarm rate of only a few percent.
Acknowledgments
Safe Zone Systems, Albuquerque, NM, is the sole sponsor for this program. The microwave assembly is manufactured by Mid Atlantic RF System, Forrest Hill, MD. The patch antenna assembly is manufactured by JEM Engineering, Laurel, MD. The system has been completely designed by and all technical support provided by Electro Science Technologies, Albuquerque, NM.
