Modern quantum technology opens up many new areas of application. But it also harbors risks. Due to their enormous computing power, quantum computers, could undermine even the most modern data encryption methods. To forestall this scenario, several partners led by KEEQuant GmbH are developing a new approach to secure optical data transmission in wireless networks using light and quantum keys. The "QuINSiDa" project is funded by the German Federal Ministry of Education and Research BMBF with a sum of 2 million euros.
With quantum technology, the next leap innovations are on the horizon in many technical areas. In addition to quantum computers, quantum imaging and quantum clocks, developments are focusing primarily on quantum communication and quantum encryption for secure and private data communication. Here, classical encryption approaches based on computational complexity are to be replaced by novel quantum key distribution approaches in combination with post-quantum cryptography. This type of encryption cannot be cracked even with arbitrary time and computational power. Since existing cryptography is already threatened in the near future by the ever-increasing computational power of quantum computers, solution approaches must be developed in time to prevent an insecure transition period.
Previous research has focused on long-distance secure data communication for applications in the global data infrastructure, for networking government or military facilities, or for information exchange with satellites. However, the connections to the end user on the last kilometer have so far still been served by classical technologies and thus remain vulnerable to attack. To prevent this in the future, the project "QuINSiDa - Quantum-based Infrastructure Networks for Safety-critical Wireless Data Communication" was launched. The project, funded by the BMBF, has a planned duration from 01.09.2022 to 31.08.2025.
Linking Li-Fi technology and quantum cryptography
Li-Fi technology allows users to network with each other over short distances using optical signals. Compared to the familiar Wi-Fi technology, which is based on radio waves, the optical signals do not penetrate walls and can thus be designed for a defined area. Li-Fi technology thus allows full utilization of the available spectral data bandwidth in this area without interference from outside.
Independent of this, the novel technology of quantum cryptography is being advanced worldwide. In specific, this involves quantum key distribution (QKD), which makes it possible to distribute a cryptographic key whose security can be proven from an information-theoretic point of view. This contrasts with existing cryptographic techniques, whose security is based on computational complexity and is compromised by emerging quantum computers.
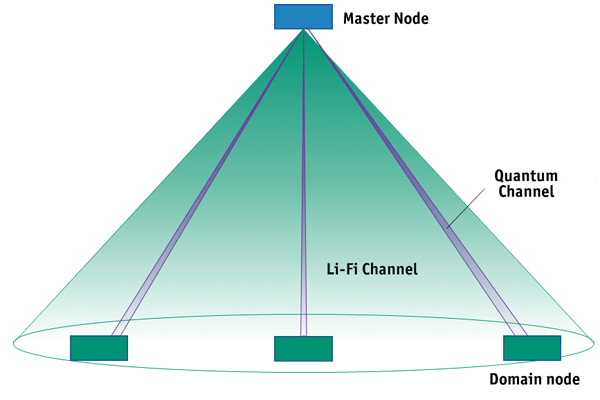
In QKD, quantum states in the form of light are prepared and exchanged between participants in the network when the keys are generated. When the quantum states are received, they are measured and post-processed to produce keys that are identical on both sides but secret to an attacker. The QuINSiDa project is the first to combine both technologies into a "QKD over Li-Fi" system. This makes it possible to carry QKD, which until now has typically been thought of more in a building-to-building scenario, all the way to the end user.
"The intention of the project is to demonstrate a quantum-based data communication network that wirelessly and flexibly connects multiple end users to a secure backbone infrastructure or which can be deployed separately as a secure campus network," says Imran Khan, Managing Director of KEEQuant GmbH. The idea is to use a flexible wireless data communication network in a point-to-multipoint scenario to simultaneously secure the individual communication channels based on quantum keys.
Technology application
In contrast to radio-based approaches, the use of an optical communication network offers the advantage that every participant who registers in the optical wireless communication channel (Li-Fi channel) is also visible to the quantum channel. This ensures that secure key exchange can occur. Different wavelengths of light are used to separate the Li-Fi channel and the quantum channel. This separation can be optimized by the receiver by using appropriate optical filtering against interference.
The presented concept of a quantum-based infrastructure network for safety-critical wireless data communication is a completely new interdisciplinary approach that has not yet been presented in scientific publications or in current market solutions. The approach will be investigated by the project partners primarily with respect to security-critical applications, such as equipment for public utilities, including banks, hospitals, utilities, public services, telecommunications nodes and government facilities. Here, special attention will be paid to the security of the overall system with simultaneous, interdisciplinary integration of network management software, classical cryptography (keyword: post-quantum cryptography), QKD technology and Li-Fi technology. At the same time, considering the background of technological sovereignty, the project is of social importance for Germany as a business location.
At the end of the project, a corresponding demonstration of the overall system is planned, which will bring the technologies together in a network and thus enable previously unexplored and unachieved use cases. Following the project, these will be exploited by the participating companies and incorporated into safety-critical applications. Due to the end user focus, a broad application and thus a very large market potential and innovation potential can be identified. In addition, the drastic cost reduction in QKD that will arise in the next few years due to production in medium quantities will enable broader market penetration.
Furthermore, the interdisciplinary networking between the different communities (QKD, optics, telecommunication, security) leads to a seamless integration of the novel technologies into existing security technologies. This makes it easy for end users to adopt the technology into existing infrastructure.

